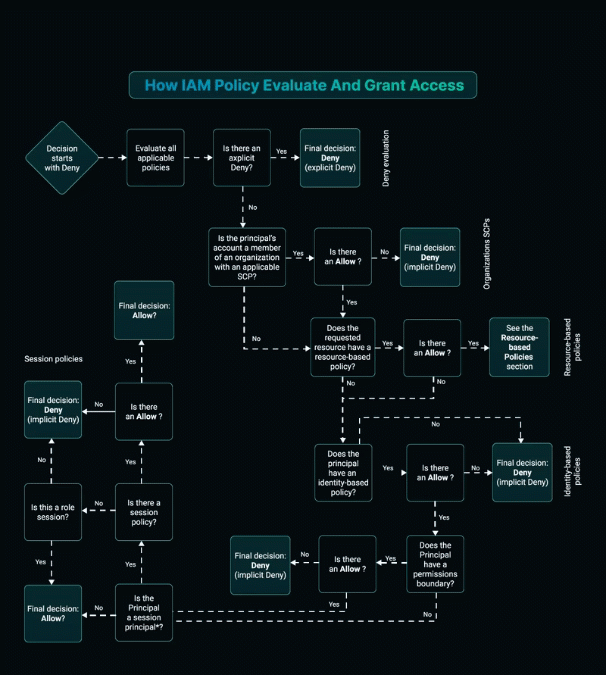
Understanding How AWS IAM Policy Evaluation Works
AWS Identity and Access Management (IAM) plays a critical role in controlling access to resources within your AWS environment. The IAM policy evaluation process follows a structured approach to determine whether access should be granted or denied. Here’s an in-depth look at each step:
1. Default Deny
At the outset, the evaluation process adopts a “default deny” stance. If no matching permissions are found, access is automatically denied as a precautionary measure.
2. Explicit Deny
The evaluation scans for any explicit “Deny” statements within the policies. If such a statement is encountered, access is immediately denied, irrespective of any subsequent “Allow” statements.
3. Organizations SCPs (Service Control Policies)
For accounts associated with an AWS Organization, the evaluation checks for Service Control Policies (SCPs). SCPs define permissions across the organization and can explicitly deny actions or implicitly deny them if not explicitly allowed.
4. Resource-based Policies
Resource-based policies, such as S3 bucket policies, are evaluated next. If the policy explicitly permits the action, the evaluation proceeds; otherwise, it moves to the next step.
5. Identity-based Policies
If no relevant resource-based policy is found, or if it doesn’t grant access, the evaluation examines identity-based policies attached to the IAM entity (user, group, or role). Access is granted if these policies allow the requested action; otherwise, it results in an implicit deny.
6. IAM Permissions Boundaries
IAM entities with permissions boundaries set undergo boundary evaluation. If the boundary restricts the action, access is implicitly denied.
7. Session Policies
For session principals like federated users or role sessions, the evaluation looks into session policies. Absence of an “Allow” in session policies results in an implicit deny; otherwise, access is granted.
In multi-account AWS Organizations, SCPs can supersede permissions in individual accounts. An explicit deny in SCPs takes precedence over any allows in identity or resource-based policies within those accounts.
The meticulous evaluation flow in AWS IAM ensures precise control over resource access. An explicit deny statement holds precedence over any allow, and in the absence of explicit allows, the default action is denial. This systematic approach upholds stringent security standards and facilitates granular control over resource access in AWS environments.
Keep visiting QuickShare and write to us in the comments below.