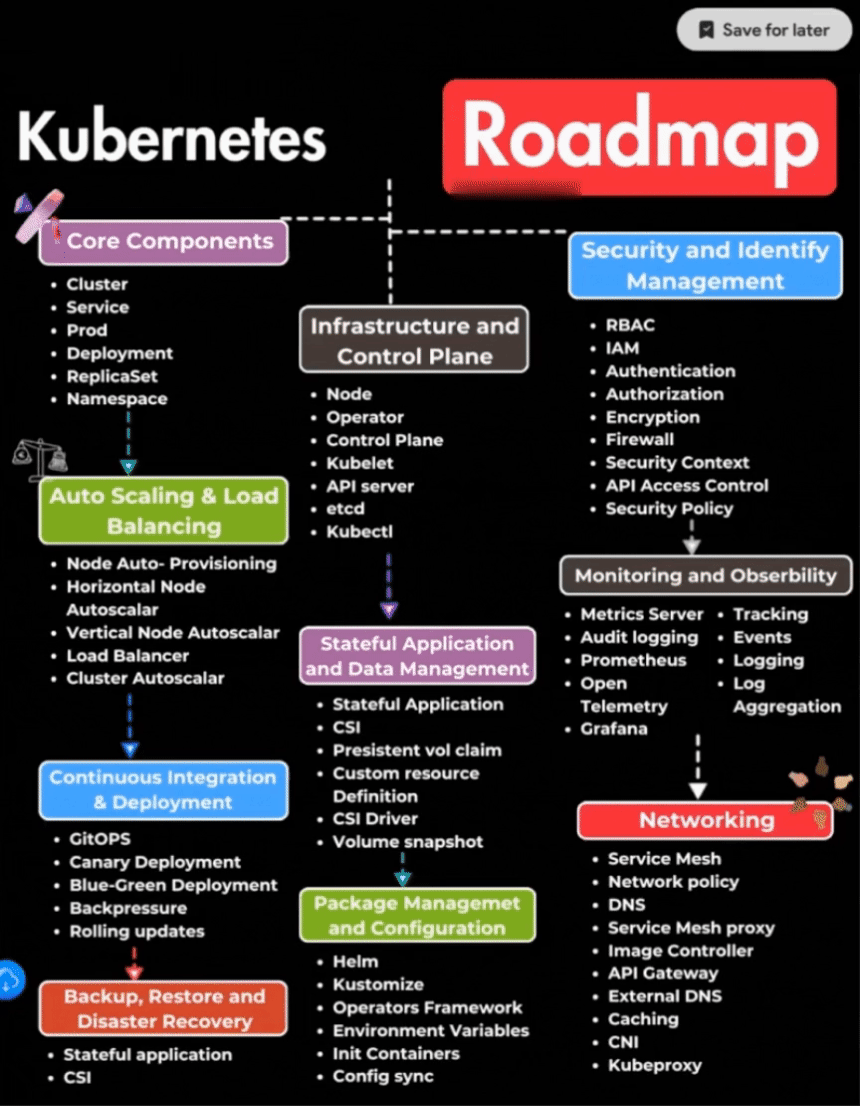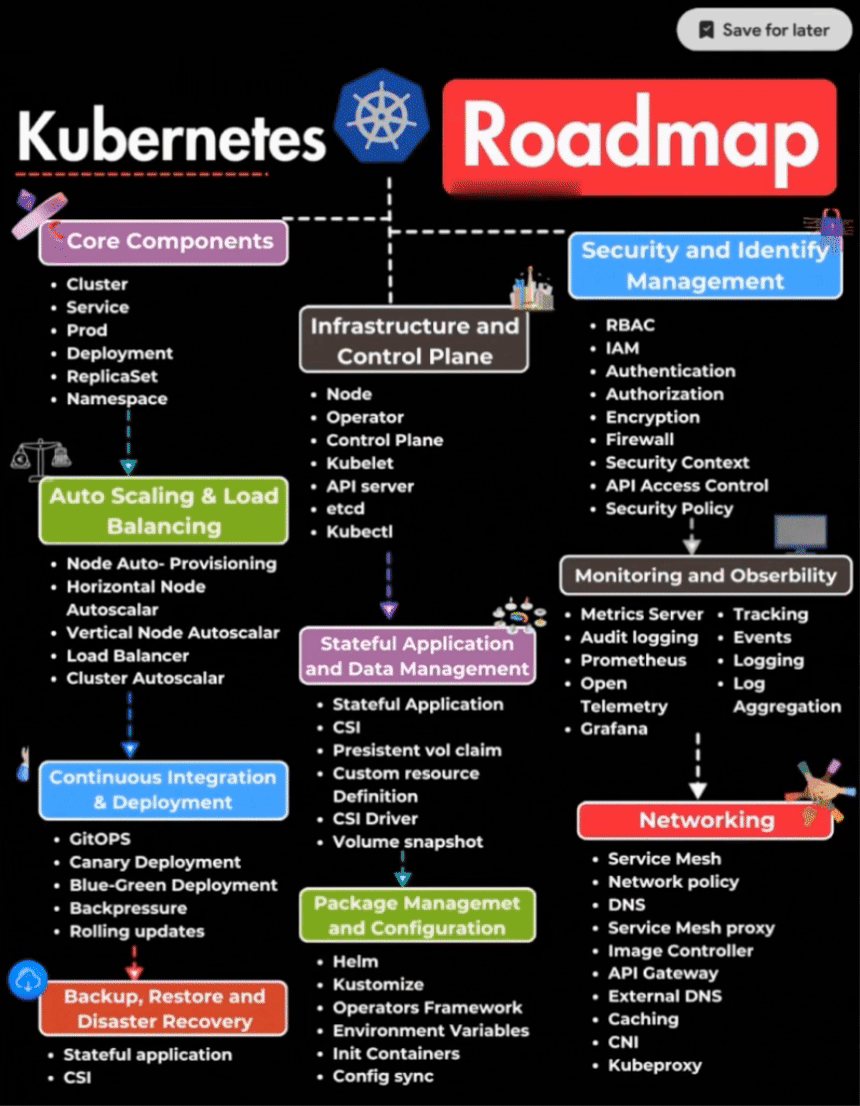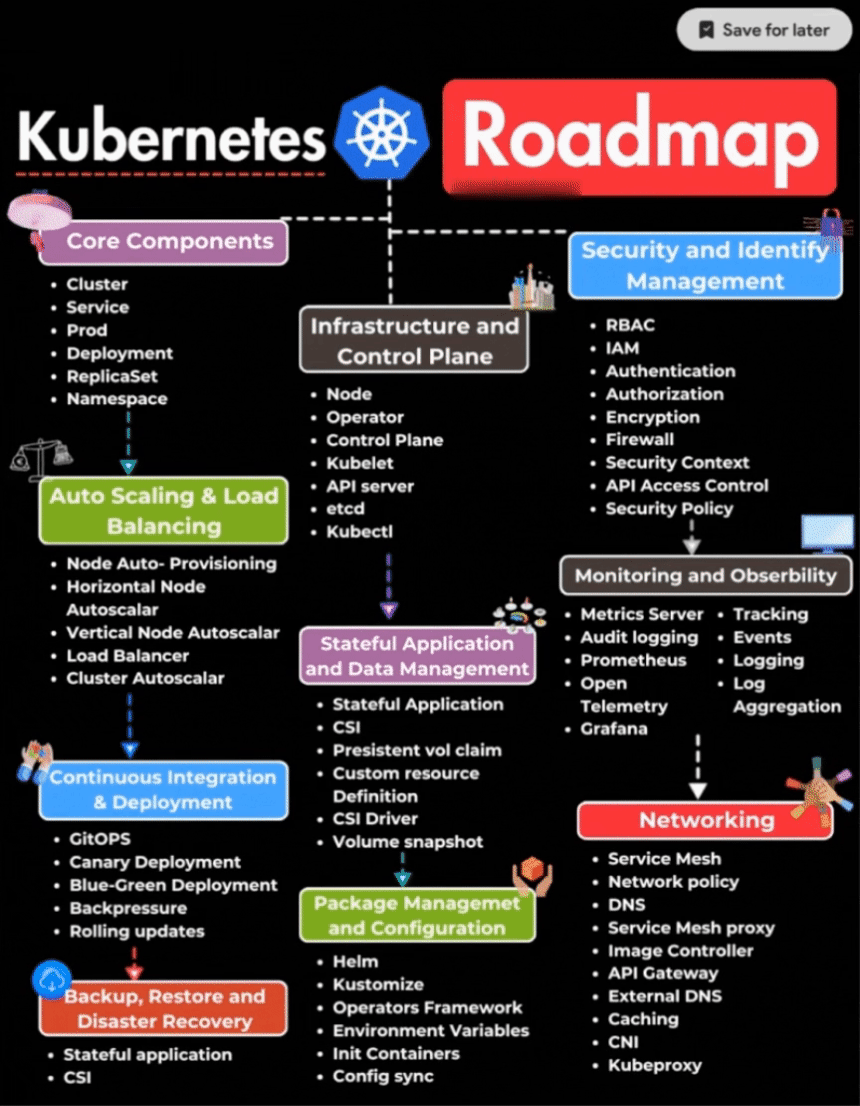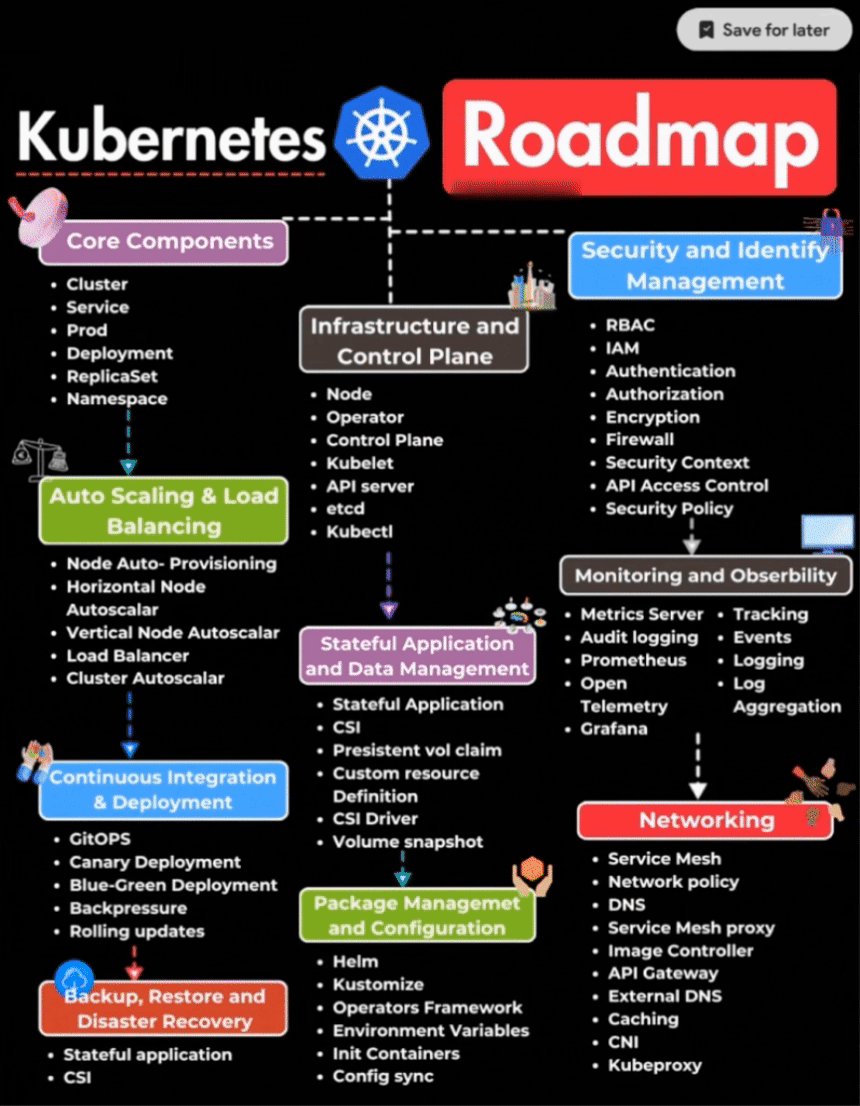
Security and Identity Management in Kubernetes
1. Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a crucial aspect of Kubernetes security, allowing administrators to define and manage user permissions within a cluster.
2. Identity and Access Management (IAM)
IAM encompasses the policies and processes that ensure the right individuals have the appropriate access to resources. In Kubernetes, IAM is pivotal for maintaining a secure environment.
3. Authentication
Authentication mechanisms in Kubernetes verify the identity of users and systems accessing the cluster, enhancing overall security.
4. Authorization
Authorization mechanisms control and grant permissions to authenticated users, specifying what actions they can perform within the Kubernetes environment.
5. Encryption
Encryption is essential for securing data in transit and at rest within a Kubernetes cluster, safeguarding sensitive information.
6. Firewall
Firewalls play a role in securing the network within Kubernetes, preventing unauthorized access, and protecting against potential threa
7. Security Context
Security Context defines and controls the security settings for Pods or containers, allowing for granular security configurations.
8. API Access Control
API access control ensures that only authorized entities can interact with the Kubernetes API server, mitigating the risk of unauthorized access.
9. Security Policy
Security policies establish guidelines and rules to ensure adherence to security standards and best practices within the Kubernetes environment.
Infrastructure and Control Plane Management
1. Node Operator
Node operators automate the management and maintenance of nodes in a Kubernetes cluster, ensuring optimal performance and resource utilization.
2. Control Plane
The control plane consists of essential components like the API server, etcd, and more, overseeing the orchestration and coordination of cluster activities.
3. Kubelet
Kubelet is a vital node agent responsible for managing and maintaining individual nodes in a Kubernetes cluster.
4. API Server
The API server acts as the gateway for communication between various components in the Kubernetes control plane and the nodes.
5. Etcd
etcd is a distributed key-value store that stores configuration data, ensuring consistency and reliability in a Kubernetes cluster.
6. Kubectl
Kubectl is the command-line interface for interacting with a Kubernetes cluster, enabling users to manage and control cluster resources.
Auto Scaling and Load Balancing
1. Node Auto-Provisioning
Node auto-provisioning automates the process of adding new nodes to the cluster based on resource demands, ensuring scalability.
2. Horizontal Node Autoscaler
Horizontal node autoscaling adjusts the number of nodes in a cluster based on resource utilization, optimizing performance.
3. Vertical Node Autoscaler
Vertical node autoscaling enhances individual node performance by adjusting resource allocation based on workload requirements.
4. Load Balancer
Load balancers distribute incoming network traffic across multiple nodes, ensuring efficient resource utilization and preventing overloads.
5. Cluster Autoscaler
Cluster autoscaling dynamically adjusts the number of nodes in a cluster to handle varying workloads and improve resource efficiency.
Continuous Integration and Deployment
1. GitOPS
GitOPS integrates Kubernetes configuration management with version control systems like Git, streamlining continuous integration and deployment processes.
2. Canary Deployment
Canary deployment gradually rolls out updates to a subset of users, allowing for monitoring and minimizing potential issues before full deployment.
3. Blue-Green Deployment
Blue-Green deployment involves running two identical production environments, enabling seamless updates and rollbacks without downtime.
4. Backpressure
Backpressure mechanisms prevent system overload by slowing down or rejecting requests during high load, ensuring stable performance.
5. Rolling Updates
Rolling updates systematically replace instances of an application, minimizing downtime and ensuring a smooth transition during updates.
6. Backup, Restore, and Disaster Recovery
Proactive measures such as regular backups and well-defined disaster recovery plans are essential for maintaining data integrity and system resilience.
Package Management and Configuration
1. Helm
Helm is a package manager for Kubernetes that simplifies the deployment and management of applications through pre-defined charts.
2. Kustomize
Kustomize offers customization of Kubernetes manifests without altering the original files, providing flexibility in configuration management.
3. Operators Framework
Operators enable the extension of Kubernetes to automate complex application management tasks, enhancing operational efficiency.
4. Environmente Variabls
Environment variables allow the configuration of application settings within containers, promoting flexibility and ease of management.
5. Init Containers
Init containers execute tasks before the main application starts, facilitating tasks like configuration, setup, or data initialization.
6. Config Sync
Config Sync ensures that the configuration stored in a Git repository is automatically synchronized with the Kubernetes cluster, maintaining consistency.
Monitoring and Observability
1. Metrics Server
The Metrics Server collects and exposes resource utilization metrics, enabling effective monitoring and optimization of Kubernetes clusters.
2. Audit Logging
Audit logging tracks activities within a Kubernetes cluster, providing insights into user actions and potential security threats.
3. Prometheus
Prometheus is an open-source monitoring and alerting toolkit designed for reliability and scalability in Kubernetes environments.
4. Open Telemetry
Open Telemetry facilitates the collection of distributed traces and metrics, offering comprehensive insights into application performance.
5. Grafana
Grafana is a popular dashboard and visualization platform, provides real-time monitoring and analytics for Kubernetes clusters.
6. Tracking, Events, and Logging
Effective tracking, event handling, and logging practices are essential for diagnosing issues and maintaining a robust Kubernetes infrastructure.
7. Log Aggregation
Log aggregation consolidates log data from various sources, streamlining troubleshooting and analysis for improved observability.
Networking
1. Service Mesh
Service Mesh enhances communication between microservices, providing functionalities like load balancing, security, and observability.
2. Network Policy
Network policies define communication rules between Pods, ensuring secure and controlled traffic within a Kubernetes cluster.
3. DNS
DNS services in Kubernetes facilitate the discovery and communication between services, promoting seamless connectivity.
4. Service Mesh Proxy
Service Mesh proxies manage communication between services, implementing features like routing, security, and resilience.
5. Image Controller
Image controllers automate the deployment and management of container images within a Kubernetes environment, ensuring consistency.
6. API Gateway
API gateways act as intermediaries between microservices, handling tasks such as routing, security, and access control.
7. External DNS
External DNS automates the management of DNS records for external services, simplifying the process of exposing applications.
8. Caching
Caching mechanisms improve performance by storing frequently accessed data, reducing the load on backend services.
9. CNI (Container Network Interface)
CNI defines how network connectivity is established between containers, ensuring seamless communication in Kubernetes clusters.
10. Kubeproxy
Kubeproxy maintains network rules on nodes, facilitating communication between Pods and ensuring proper load balancing.
Stateful Application Management and Data Management
1. CSI (Container Storage Interface)
CSI provides a standardized interface for storage systems to integrate with container orchestrators, enhancing storage management.
2. Stateful Application CSI
Stateful Application CSI allows the dynamic provisioning and management of persistent volumes for stateful applications.
3. Persistent Volume Claim
Persistent Volume Claims enable applications to request storage resources, ensuring the availability of persistent storage for Pods.
4. Custom Resource Definition (CRD)
CRDs extend Kubernetes to support custom resources, enabling the definition of custom objects and behaviors within the cluster.
5. CSI Driver
CSI drivers facilitate communication between the container orchestrator and storage systems, ensuring seamless integration.
6. Volume Snapshot
Volume snapshots capture the state of persistent volumes at a specific point in time, supporting data backup and recovery.
With a comprehensive understanding of these key aspects, you can effectively manage and secure your Kubernetes environment, ensuring optimal performance and reliability.
If you want to learn more about Kubernetes or you want to learn a more detailed understanding of these points, keep visiting QuickShare and write us in the comments below.